Dealing with a Breach Mock Crisis: Putting the Response Plan to the Test - June 4, 2015
Sullivan & Cromwell
Description
Dealing with a Breach
Mock Crisis: Putting the Response Plan to
the Test
Frank Cilluffo
Daniel M. Gallagher, Jr.
Stephen Labaton
James F. Yacone
Moderator: Jay Clayton
Attorney Advertising
Prior results do not guarantee a similar outcome.
Copyright ©2015 Sullivan & Cromwell LLP
. Child’s Toy and Clothing Co.
• Child’s Toy and Clothing Co. (“CTC”) is a Nasdaq-listed
company specializing in the sale of children’s clothing and toys.
• It has brick-and-mortar stores in 28 states and it sells its
products online to customers nationwide and in Canada and
Mexico.
• CTC has approximately 24 million online sales per year from 8
million different customers.
• CTC has a market capitalization of $2.5 billion, up from $1
billion in 2012, and sales of $1.4 billion. CTC’s sales are split
equally between its brick-and-mortar stores and its online
business, but the online business is far more lucrative—
accounting for 75% of CTC’s profits.
2
Copyright ©2015 Sullivan & Cromwell LLP
. Child’s Toy and Clothing Co.
Continued
• CTC collects and stores information from customers when
they place online orders, such as name, address and payment
card information.
• In addition, the CTC website includes a “Kids’ Zone” where,
with properly authenticated parental consent, children can
create online profiles and play games. Information gathered
from the profiles and games is used internally for targeted
advertising to the children and their parents.
• CTC’s privacy policy clearly discloses this use and states that
“CTC uses commercially reasonable physical, managerial and
technical safeguards to preserve the integrity and security of
its customers’ and users’ personal information.”
3
Copyright ©2015 Sullivan & Cromwell LLP
. Child’s Toy and Clothing Co.
Continued
• CTC’s IT systems were developed over time. On several
occasions when CTC acquired a smaller competitor, the
companies’ IT systems were merged.
• CTC’s IT team consists of a few internal personnel and is
supported by several outside vendors. CTC also has a Chief
Information Security Officer (“CISO”) who was hired in early
2013.
• CTC has a cyber incident response plan, which was last
reviewed with senior management and the board of directors
in November 2014.
• CTC subscribes to cyberinsurance.
4
Copyright ©2015 Sullivan & Cromwell LLP
. Notice of Potential Data Breach
• On Friday, June 12th, CTC is informed by its credit card
processor that the processor has detected a pattern of
fraudulent payment card activity following customer
purchases on CTC’s online store.
What are the first steps CTC should take and how should CTC
begin assessing the potential breach?
June 12:
Notice of
Breach
5
Copyright ©2015 Sullivan & Cromwell LLP
. Confirmation of Data Breach
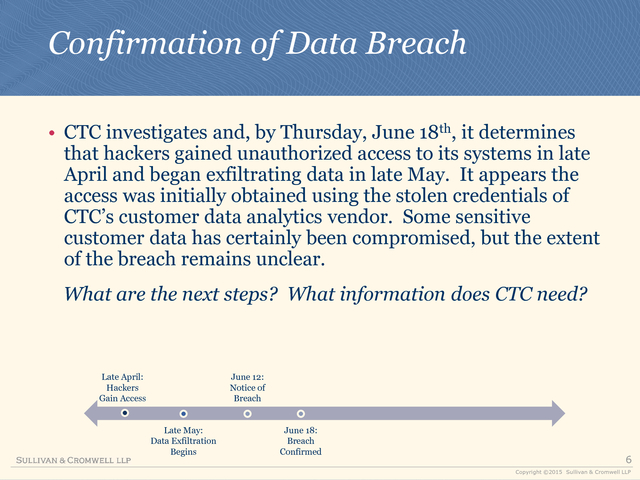
• CTC investigates and, by Thursday, June 18th, it determines
that hackers gained unauthorized access to its systems in late
April and began exfiltrating data in late May. It appears the
access was initially obtained using the stolen credentials of
CTC’s customer data analytics vendor. Some sensitive
customer data has certainly been compromised, but the extent
of the breach remains unclear.
What are the next steps? What information does CTC need?
Late April:
Hackers
Gain Access
June 12:
Notice of
Breach
Late May:
Data Exfiltration
Begins
June 18:
Breach
Confirmed
6
Copyright ©2015 Sullivan & Cromwell LLP
. The Compromised Data
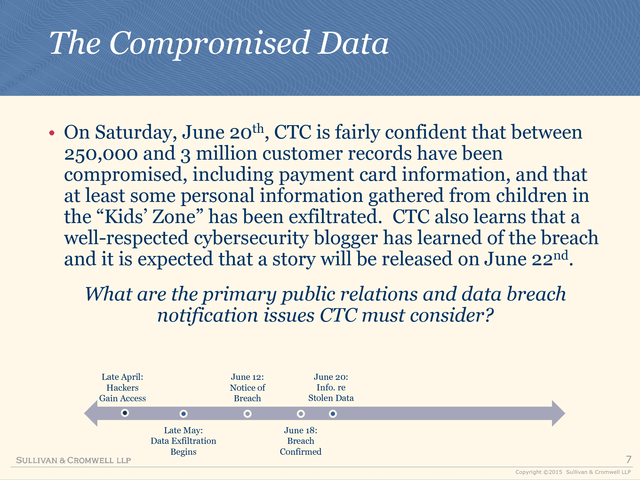
• On Saturday, June 20th, CTC is fairly confident that between
250,000 and 3 million customer records have been
compromised, including payment card information, and that
at least some personal information gathered from children in
the “Kids’ Zone” has been exfiltrated. CTC also learns that a
well-respected cybersecurity blogger has learned of the breach
and it is expected that a story will be released on June 22nd.
What are the primary public relations and data breach
notification issues CTC must consider?
Late April:
Hackers
Gain Access
June 12:
Notice of
Breach
Late May:
Data Exfiltration
Begins
June 20:
Info. re
Stolen Data
June 18:
Breach
Confirmed
7
Copyright ©2015 Sullivan & Cromwell LLP
. Stock Drop and SEC Disclosures
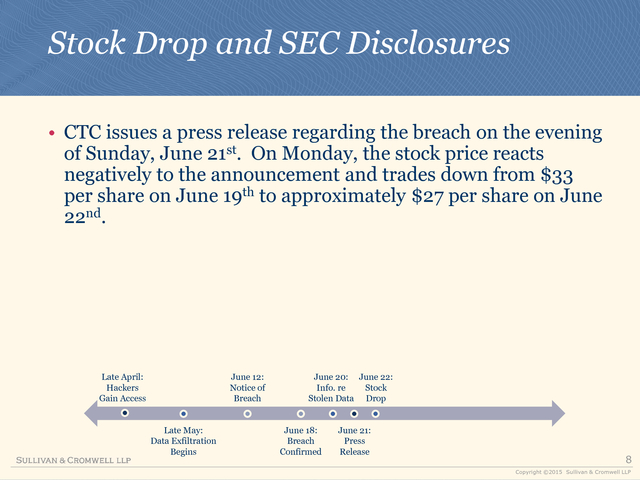
• CTC issues a press release regarding the breach on the evening
of Sunday, June 21st. On Monday, the stock price reacts
negatively to the announcement and trades down from $33
per share on June 19th to approximately $27 per share on June
22nd.
Late April:
Hackers
Gain Access
June 12:
Notice of
Breach
Late May:
Data Exfiltration
Begins
June 20: June 22:
Info. re
Stock
Stolen Data Drop
June 18:
Breach
Confirmed
June 21:
Press
Release
8
Copyright ©2015 Sullivan & Cromwell LLP
. Stock Drop and SEC Disclosures
Continued
• It is now July 2nd and CTC’s stock continues to trade in the
$26-28 range. The company has determined that online sales
sharply declined at the end of June and that the company’s
quarterly earnings will be 5-10% below the consensus estimate
of analysts. CTC’s next scheduled earnings call and 10-Q filing
are on July 15th and 31st, respectively.
What steps should CTC consider taking?
Late April:
Hackers
Gain Access
June 12:
Notice of
Breach
Late May:
Data Exfiltration
Begins
June 20: June 22:
Info. re
Stock
Stolen Data Drop
June 18:
Breach
Confirmed
June 21:
Press
Release
July 15:
Next Sched.
Earnings Call
July 2:
Info.
re Earnings July 31: Next Sched. 10-Q Filing 9 Copyright ©2015 Sullivan & Cromwell LLP . Liability Exposure Continued • As the dust begins to settle, CTC is assessing its regulatory and civil liability exposure as a result of the breach. What are some of the issues it must consider? Late April: Hackers Gain Access June 12: Notice of Breach Late May: Data Exfiltration Begins June 20: June 22: Info. re Stock Stolen Data Drop June 18: Breach Confirmed June 21: Press Release July 15: Next Sched. Earnings Call July 2: Info. re Earnings July 31: Next Sched. 10-Q Filing 10 Copyright ©2015 Sullivan & Cromwell LLP . .
re Earnings July 31: Next Sched. 10-Q Filing 9 Copyright ©2015 Sullivan & Cromwell LLP . Liability Exposure Continued • As the dust begins to settle, CTC is assessing its regulatory and civil liability exposure as a result of the breach. What are some of the issues it must consider? Late April: Hackers Gain Access June 12: Notice of Breach Late May: Data Exfiltration Begins June 20: June 22: Info. re Stock Stolen Data Drop June 18: Breach Confirmed June 21: Press Release July 15: Next Sched. Earnings Call July 2: Info. re Earnings July 31: Next Sched. 10-Q Filing 10 Copyright ©2015 Sullivan & Cromwell LLP . .